DDoS Defense Systems in Large Enterprises: A Comprehensive Review of Adoption, Challenges, and Strategies
Keywords:
Control structure, Defense location, DDoS attacks, Infrastructure-based defense, Large enterprises, Layered defense approach, Misuse detection techniqueAbstract
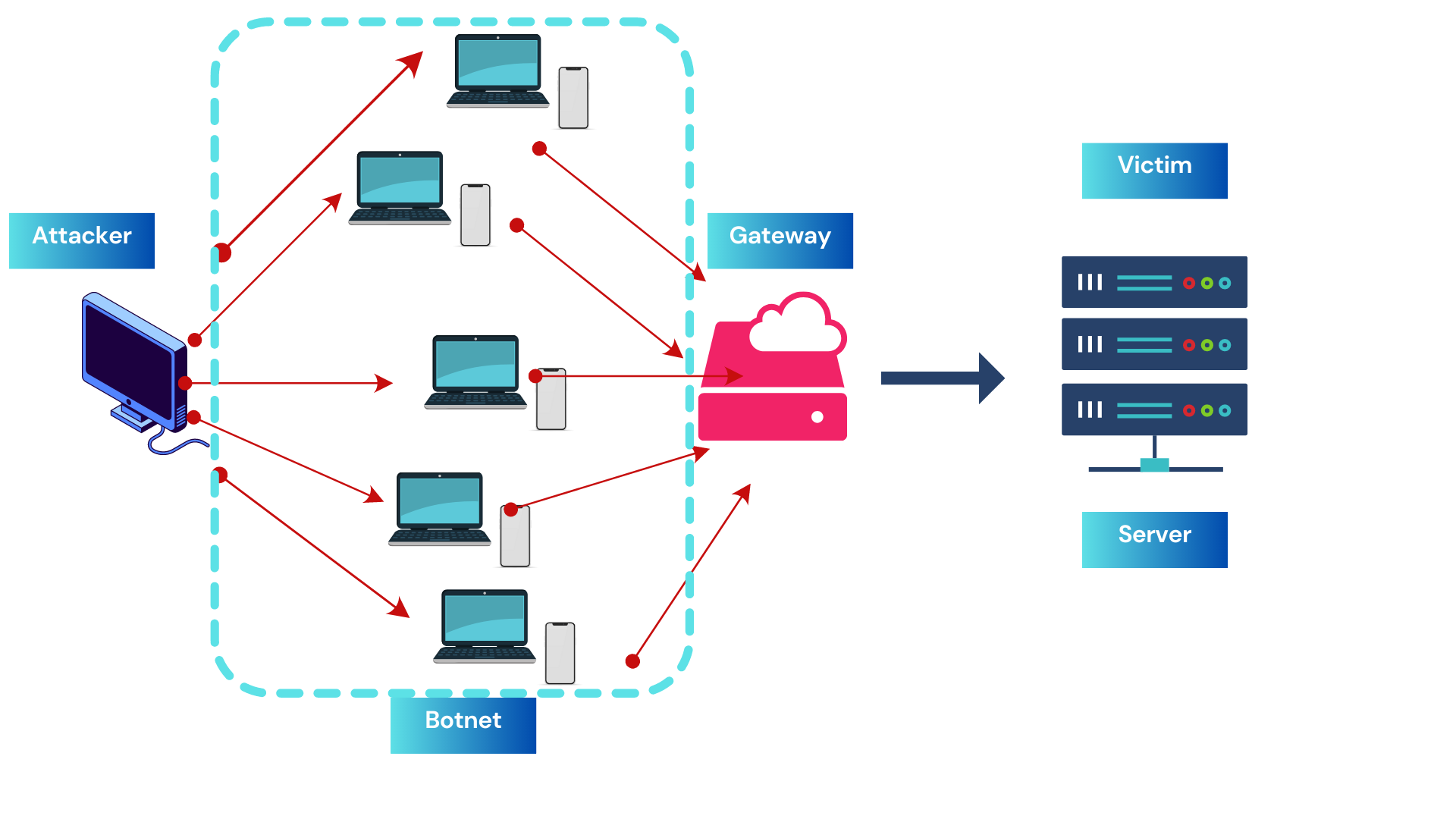
This research aims to review and discuss the adoption, challenges, and strategies of large enterprises regarding five categories related to DDoS attacks: approaches to confronting DDoS attacks, control structure used to counterattack traffic, infrastructure-based DDoS defense, based on defense location, and based on technique used. The findings of this study provide insights into the strategies that large enterprises can adopt to overcome the challenges and provide effective protection against DDoS attacks. Regarding approaches to confronting DDoS attacks, large enterprises need to adopt a multi-layered approach that includes investing in advanced hardware and software capabilities, implementing a threat intelligence program, and adopting a proactive approach to testing and improvement. This approach can help prevent DDoS attacks and mitigate their impact. In terms of control structure used to counterattack traffic, three types were discussed: centralized, hierarchical, and distributed DDoS defense. Each type presents challenges, but careful planning and execution, along with the adoption of best practices, can ensure the security and stability of enterprise networks. Infrastructure-based DDoS defense was also analyzed, with two types discussed: host-based and network-based DDoS defense. Enterprises need to adopt a layered approach, employing automation and orchestration tools, and employing continuous monitoring and threat intelligence to ensure effective defense against DDoS attacks. Based on defense location, three types were discussed: victim-end, intermediate network, and source-end DDoS defense. The study recommends that enterprises adopt a layered defense approach, implement network segmentation, zero-trust security, and use advanced technologies like machine learning to ensure effective protection against DDoS attacks. The study also discussed the misuse detection technique, which is used to prevent DDoS attacks by investing in hardware-based systems and updating rule sets regularly to adapt to new attack patterns. Enterprises need to implement a layered defense approach that includes both misuse and anomaly detection techniques and cloud-based DDoS protection services to provide cost savings and faster response times.
Downloads
Published
How to Cite
Issue
Section
License
CC Attribution-NonCommercial-ShareAlike 4.0



